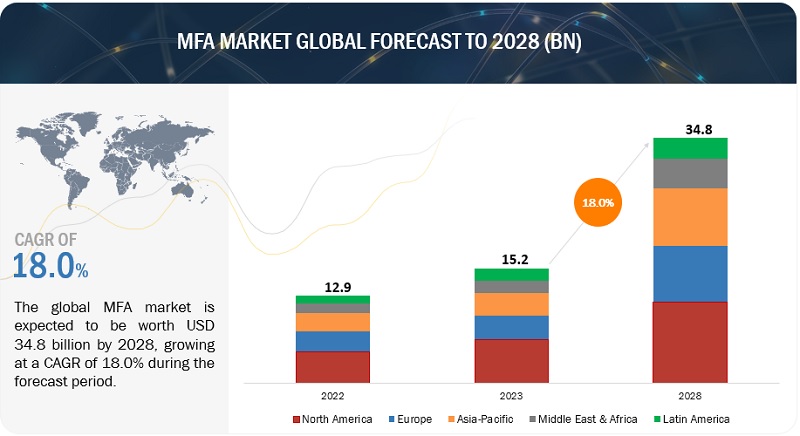
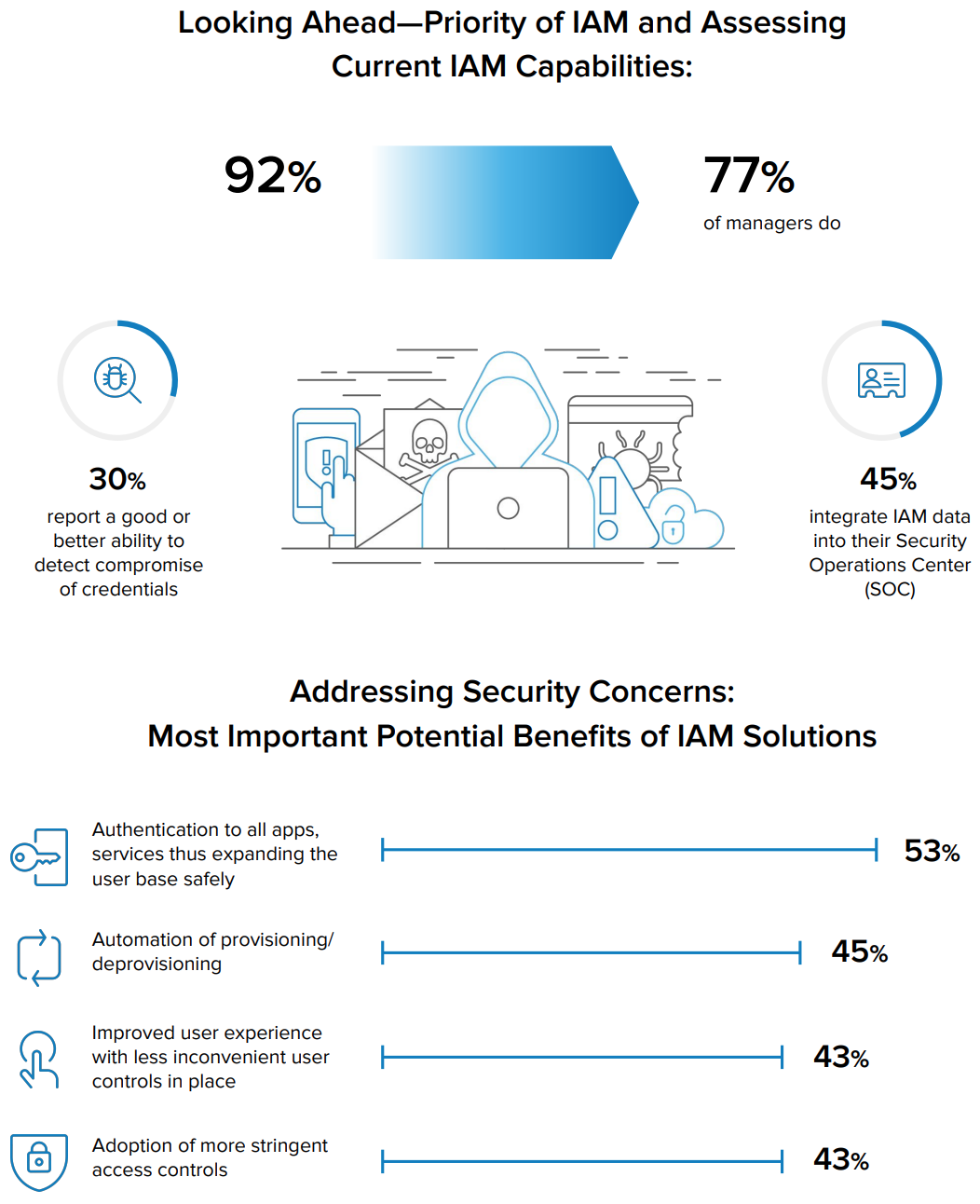
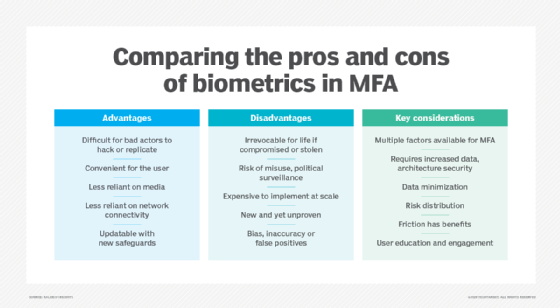
SAP SuccessFactors Two-Factor Authentication (TOTP) for Password user's integration via SAP Cloud Platform Identity Authentication (IAS) with Microsoft Authenticator App and Technical Step by Step guide | SAP Blogs

SAP SuccessFactors Two-Factor Authentication (TOTP) for Password user's integration via SAP Cloud Platform Identity Authentication (IAS) with Microsoft Authenticator App and Technical Step by Step guide | SAP Blogs
Protect Yourself With Multi-Factor Authentication - Bitcoin Magazine - Bitcoin News, Articles and Expert Insights

CVE-2020-2021: Palo Alto Networks PAN-OS Vulnerable to Critical Authentication Bypass Vulnerability - Blog | Tenable®

Protect Yourself With Multi-Factor Authentication - Bitcoin Magazine - Bitcoin News, Articles and Expert Insights